How to recover secret key from Drone CI/CD PostgreSQL DB
I run Drone as my CI/CD depoyment platform for my home Kubernetes cluster. It’s a nice and simple platform to use that integrates with my gitea environment painlessly.
One issue I have had a few times has been (through lack of my own password management) I have implemented a repository secret key into my configuration and then not noted the secret in my password manager. This causes an issue if I want to re-use the key in a different repo within Drone as the UI does not let you display the key once it has been saved (great for security though!)
This post assumes you’re running your drone setup inside of docker, or a kube cluster, though is applicable to any of the deployment types backed by PostgreSQL
First up you need to be able to connect to the PostgreSQL DB container and log in:
psql -U drone -W
enter password:
Then connect to your drone DB (mine is called drone)
\c drone
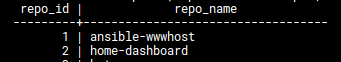
Then you need to find the repo_id of the repo you wish to recover the secret from, you can do this with:
select repo_id,name from repos;
Giving you an output like:
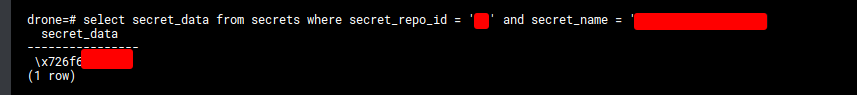
Then we want to select the secret from the secret table, using the repo ID from the previous step:
select secret_data from secrets where secret_repo_id = ID and secret_name = 'UI_SECRET_NAME>';
Giving you an output like this:
This value in the DB is your secret, however drone encodes it in hexadecimal format, which thankfully is very easy to reverse engineer. For this I’m going to use a linux tool called xxd
Remove the \x on the front of the string, and then you can run the command:
echo 'stringhere' | xxd -r -p
This will then print out your secret contents in string format! You could also use any online hex decoder service, but I prefer to keep my data local for security reasons.